One of the important tasks while performing mobile application security assessments is to be able to intercept the traffic (Man in The Middle, MiTM) between the mobile application and the server by a web proxy like Fiddler, Burp etc… This allows penetration tester to observe application behavior, modify the traffic and overcome the input restrictions enforced by application’s user interface to perform a holistic penetration test.
Mobile applications exchanging sensitive data typically use HTTPS protocol for data exchange as allows them to perform server authentication to ensure a secure communication channel. The client authenticates the server by verifying server’s certificate against its trusted root certificate authority (CA) store and also checks the certificate’s common name against the domain name of the server presenting the certificate. To perform MiTM on the HTTPS traffic for mobile application, web proxy’s certificate is imported to the trusted root CA store otherwise the application may not function due to certificate errors.
On a recent Android application assessment, I setup a web proxy to intercept mobile application’s SSL traffic by importing its certificate to device’s trusted root CA store. To ensure that the imported CA certificate works fine, I used Android’s browser to visit a couple of SSL based websites and the browser accepted the MiTM’ed traffic without complains. Typically, the native Android applications also use the common trusted root CA store to validate server certificates, so no extra work is required to intercept their traffic. However, the application I was testing was different as we will see below.
Analyzing the Unsuccessful MiTM
When I launched the application and attempted pass its traffic through the web proxy, it displayed an error screen indicating that it could not connect to the remote server because of no internet connection or it could not establish a connection for unknown reasons. Things were not adding up as this configuration has mostly worked in the past so I turned to analyzing systems logs and SSL cipher suite support.
Logcat
Logcat is Android’s logging mechanism that is used to view application debug messages and logs. I ran adb logcat to check if the application under test created any stack trace indicating the cause of the error but there was none. The application also did not leave any debug logs indicating that the developers did a good job with the error handling and did not write debug messages that could potentially expose application internal working to prying eyes.
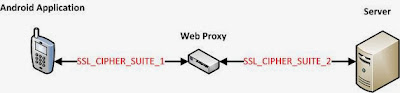
Common SSL Cipher suites
When a web proxy acts as a MiTM between client and the server, it establishes two SSL communication channels. One channel is with the client to receive requests and return responses, the second channel is to forward application requests to the server and receive server responses. To establish these channels, the web proxy has to agree on common SSL cipher suits with both the client and the server and these cipher suites may not be the same as shown in the image below.
I have observed SSL proxying errors in the past to occur in one or both of the following scenarios which lead to failures while establishing a communication channel.
- Android application and the web proxy do not share any common SSL cipher suite.
- The web proxy and the server do not share any common SSL cipher suite.
In both scenarios, the communication channel cannot be established and the application does not work. To analyze the above mentioned scenarios, I fired up Wireshark to analyze SSL handshake between the application and the web proxy, and discovered that they shared common SSL cipher suites.
With the first scenario ruled out, I issued a HTTPS request to the server with the web proxy and that appeared to work without any errors indicating presence of common SSL ciphers between web proxy and the server.
So the web proxy was capable of performing MiTM for the test application and there was something else going under the hood.
Custom Certificate Validation
It was at this point that I started to look into the possibility of the application performing custom certificate validation to prevent the possibility of MiTM to monitor/modify its traffic flow. HTTPS clients can perform custom certificate validation by implementing the X509TrustManager interface and then using it for its HTTPS connections. The process of creating HTTPS connections with custom certificate validation is summarized below:
- Implement methods of the X509TrustManager interface as required. The server certificate validation code will live inside the checkServerTrusted method. This method will throw an exception if the certificate validation fails or will return void otherwise.
- Obtain a SSLContext instance.
- Create an instance of the X509TrustManager implementation and use it to initialize SSLContext.
- Obtain SSLSocketFactory from the SSLContext instance.
- Provide the SSLSocketFactory instance to setSSLSocketFactory method of the HttpsURLConnection.
- Instance of HttpsURLConnection class will then communicate with the server and will invoke checkServerTrusted method to perform custom server certificate validation.
Searching the decompiled code revealed X509TrustManager implementation in one of the core security classes of the application. The next step was to patch the code preventing the MiTM and deploy it for testing. The image two methods implemented for X509TrustManager.
Patching the checkServerTrusted Implementation
The image above shows implementation for two X509TrustManager methods, checkServerTrusted and checkClientTrusted. At this point it is important to point out that both the methods behave in a similar way except that the former is used by client side code and the latter is used by server side code. If the certificate validation fails, they would throw an exception, otherwise they return void.
The checkClientTrusted implementation allows the server side code to validate client certificate. Since this functionality is not required inside the mobile application, this method was empty and returned void for the test application; which is equivalent to successful validation. However, the checkServerTrusted contained significant chunk of code performing the custom certificate validation which I needed to bypass.
To bypass certificate validation code inside the checkServerTrusted method, I replaced its Dalvik code with the code from the checkClientTrusted method to return void, effectively bypassing the custom certificate check as shown in the image below.
Recompiling and Deploying the Modified Application
Confident that all checkServerTrusted invocations from this point onwards were going to be successful, I recompiled the application with ApkTool, signed it with SignApk and deployed it on the device. The web proxy MiTM worked like a charm and I was able view, modify and fuzz application traffic.